Protecting and storing your AMIMOTO server keyfile
safe and secure by modify it's permissions and storing it in your SSH home folder
Whether you've created an AMIMOTO AMI or you are a AMIMOTO Managed Hosting customer you'll need a keyfile to connect to your server. If you're not familiar with how to secure and store your SSH keys here's how.
Protecting your keyfile
For Managed Hosting customers you'll receive a keyfile to connect to your server. This keyfile can be found and downloaded from your AMIMOTO Dashboard and Server Info panel.
If you are an AMIMOTO AMI Self-Hosting customers on AWS, your keyfile would either be downloaded or created during the server launch or stored from a previous launch.
Either way, protecting that keyfile is the same process.
- If you're on a Mac, start by opening Terminal and navigate to where your keyfile is located. In my case it was located in the home directory.
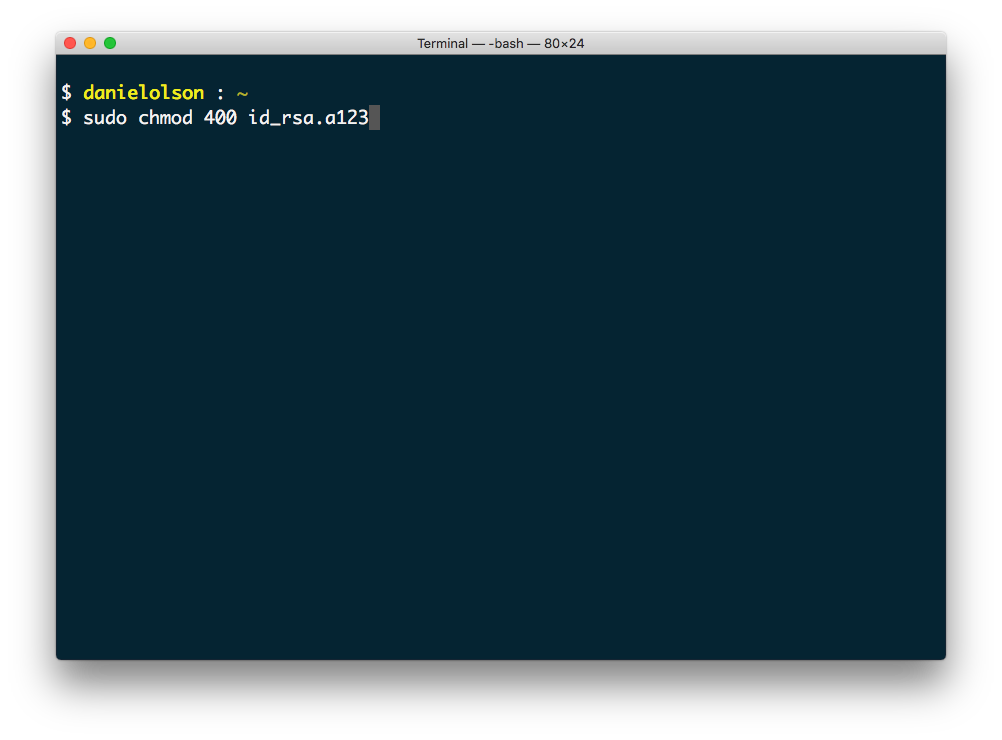
- Using the command chmod can modify the permissions of that keyfile. Our keyfile name is id_rsa.a123 the command we'll use is:
sudo chmod 400 id_rsa.a123
This command will elevate our privileges using sudo which allows us to modify the keyfile with the chmod command.
The 400 part of that command means that the keyfile will be read only by your account. This is important because it will protect that keyfile from other programs or prying eyes.
For AMI users, your keyfile command might look something like:
sudo chmod 400 keyfile.pem
You'll be required your Mac's administrator password. For more details about admin's password, please check Apple's document: Using the sudo command in Terminal requires an administrator password - Apple Support
Adding your keyfile to your ssh-agent
Sometimes it's helpful to add your keyfile to your ssh-agent because it will allow you to SSH or access servers by SFTP without explicitly declaring which keyfile to use and where it's located.
For example, declaring your keyfile with the following command:
ssh amimoto-ami@a123.pilott.amimoto-ami.com
Verses, using something like:
ssh -i path/to/id_rsa.a123 amimoto-user@a123.pilott.amimoto-ami.com
It might not seem like a big difference but when you're moving directories or just want to save time using the ssh-add command can be helpful.
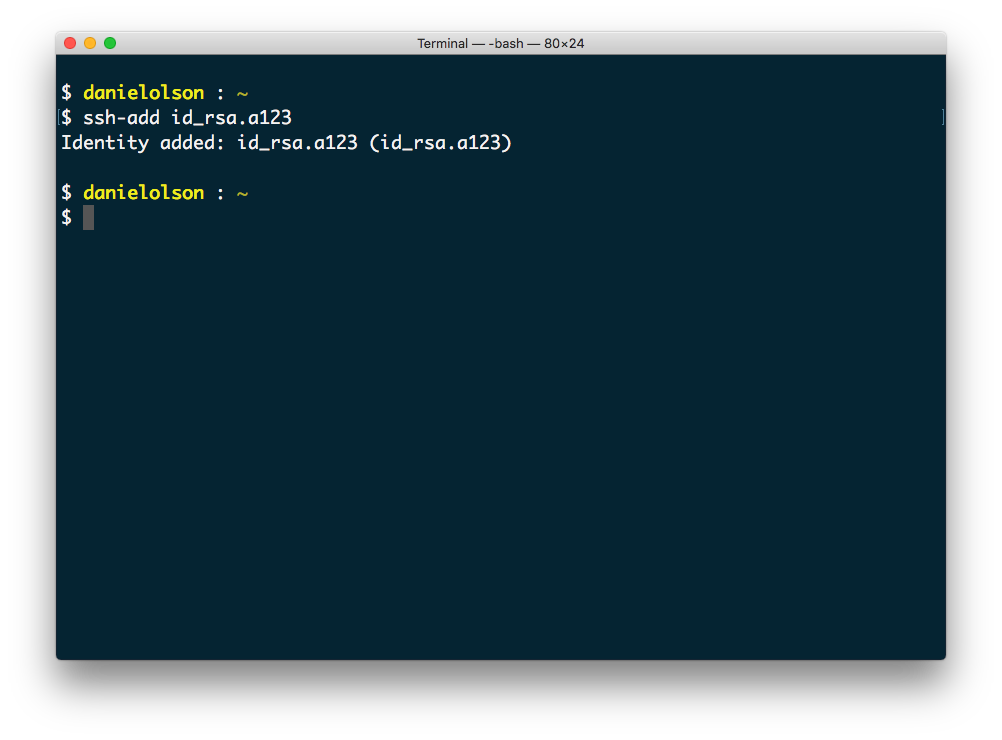
- If you're on a Mac, start by opening Terminal and navigate to where your keyfile is located. In my case it was located in the home directory.
- Use the command ssh-add to add your keyfile to your ssh-agent. In our case the keyfile name is id_rsa.a123 and it's located in the home directory.
This command only works if your ssh-agent is running. You can check or start for that with the following command
Moving your keyfile to a safe location
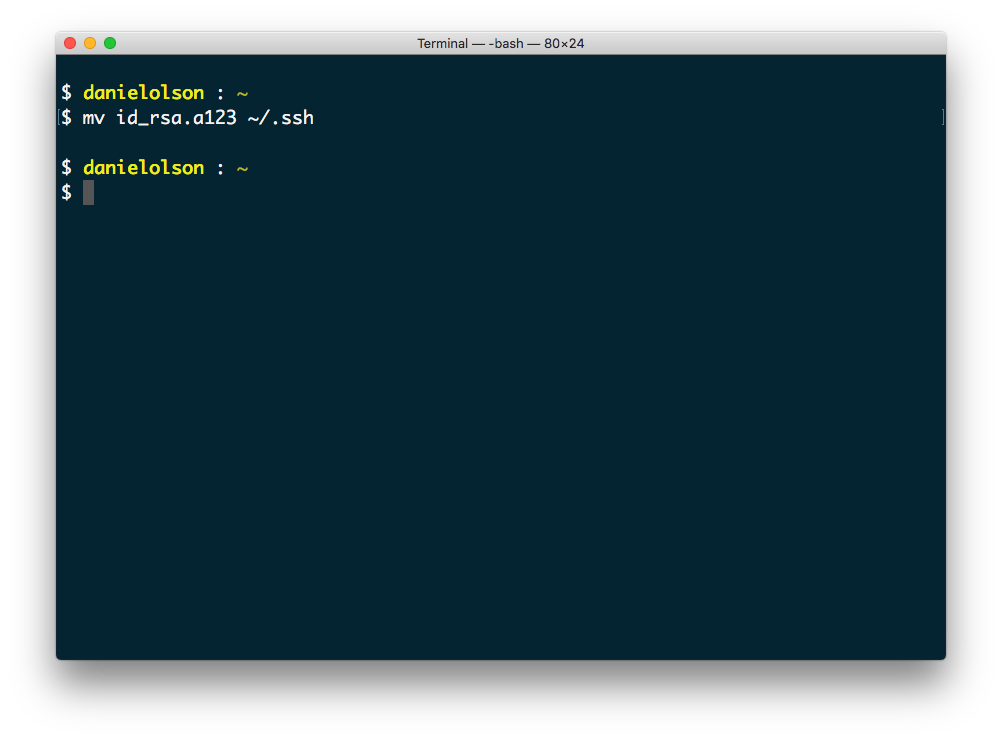
On a Mac and in your home directory is a hidden folder named .ssh. This folder contains your personal ssh keys, host files, and more.
This is an common spot for storing your keyfile and you can move it there with the following command using Terminal.
This will use the mv command to move the id_rsa.123 file to your home directory, which is the tilde part and the hidden ssh folder.
As you create or launch new AMIMOTO servers it's an easy place to reference and store your protected keyfile.
 Did this answer your question?
Did this answer your question?